Recon Scan | CyberLab Control | Cyber Security as a Service
Recon Scan
Introducing the all-in-one attack surface monitor from CyberLab Control.
Recon Scan thinks like a hacker. It uncovers all your online assets and provides a complete picture of your attack surface.
Recon Scan then scans your online assets for known vulnerabilities to identify security weaknesses, missing updates, and misconfigurations, so you can see where a real-life hacker could gain access.
Map, manage and minimise your attack surface with Recon Scan.
35 days
Average time to remediate Critical vulnerabilities in large organisations
85.5%
Of all web assets have at least one vulnerability, 8.5% have over a hundred
48%
Of vulnerabilities in large organisations remain unresolved over 12 months
Map
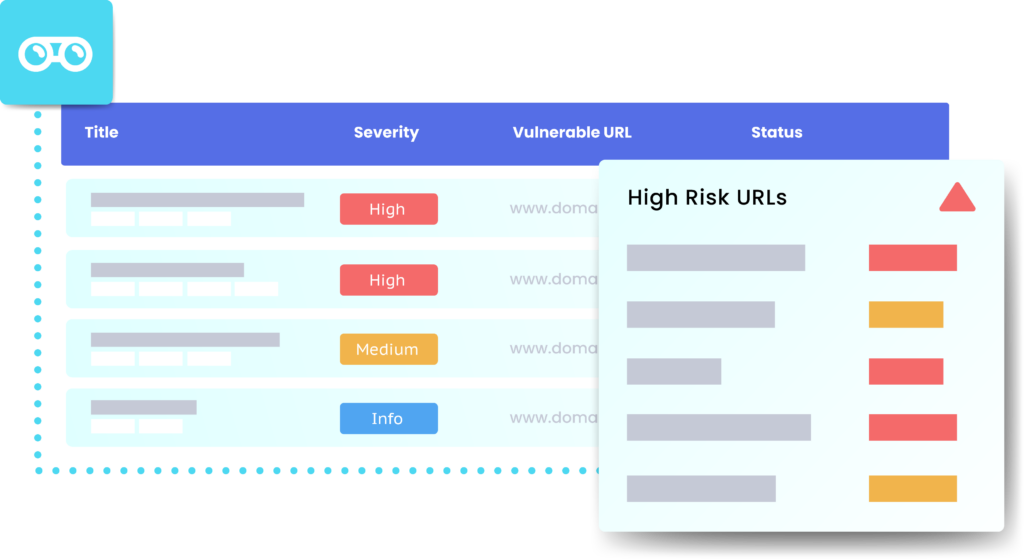
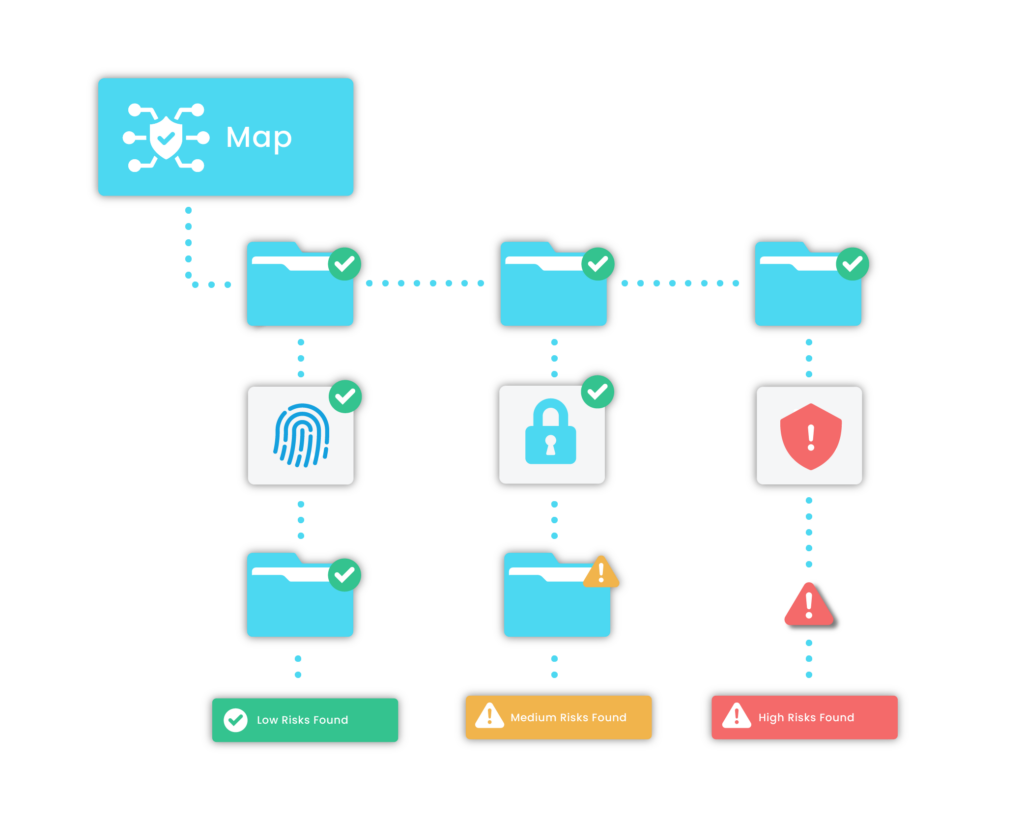
Recon Scan maps your entire external digital footprint to identify every asset you control that’s available over the internet, including;
• Subdomains
• Endpoints
• IP addresses
• Open ports
You’ll see every asset discovered, its digital location, and its current status.
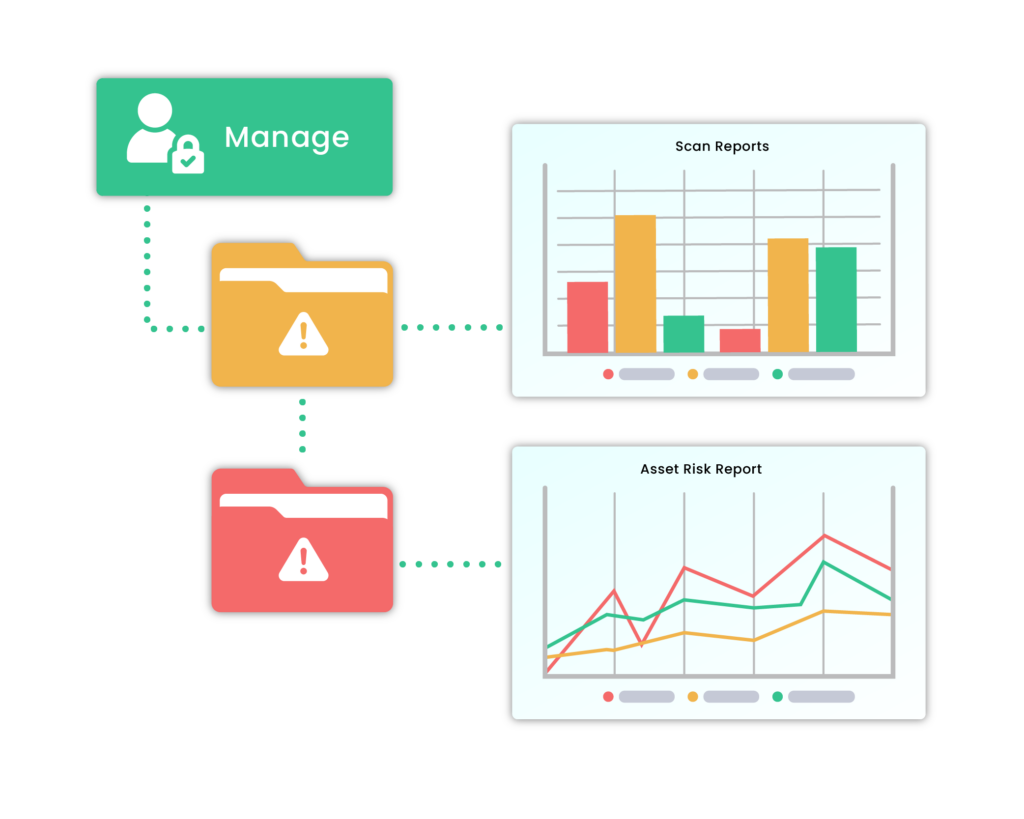
Manage
Gain the information and analysis you need to manage the vulnerabilities identified across your estate.
Every vulnerability identified by Recon Scan are explained and ranked by criticality for your attention.
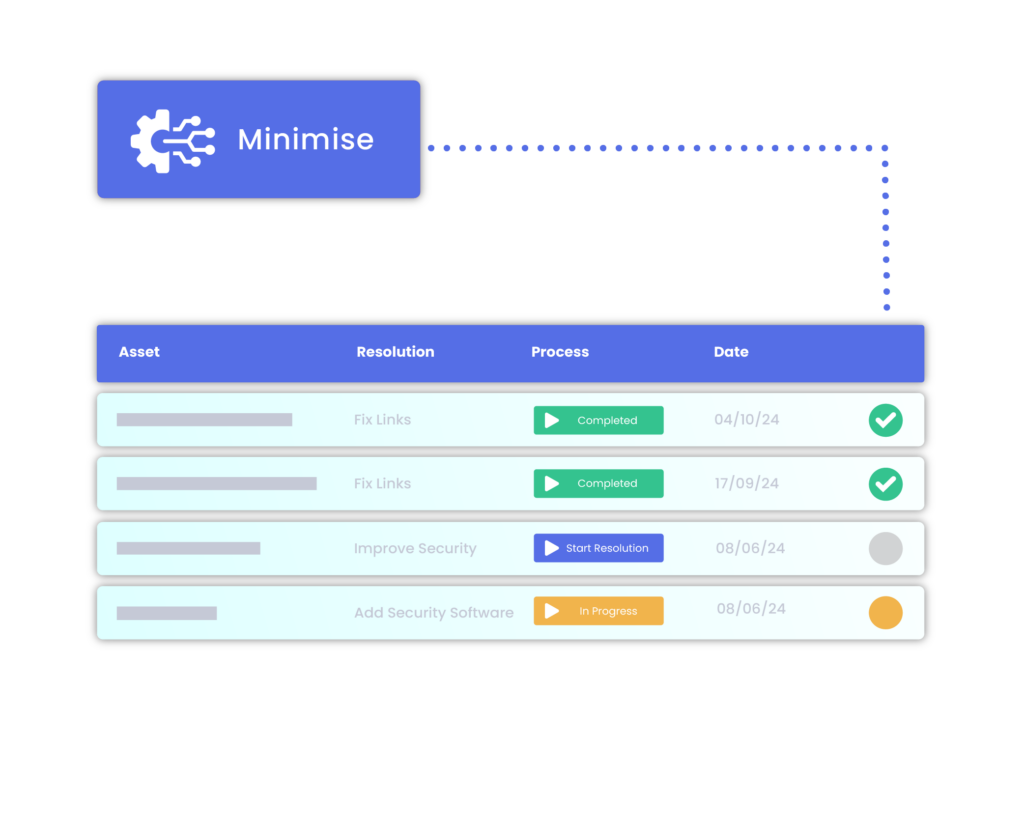
Minimise
Assign roles to your team and tackle vulnerabilities with our expert remediation advice.
Integrate with Discord, Slack, or Telegram for real-time alerts when new subdomains or vulnerabilities are discovered and start to minimise your attack surface.
Recon Scan | CyberLab Control
Free 30-day Trial
To see the impact Recon Scan could have on your organisation’s security first-hand, reach out today to arrange your free demo scan.
No obligation, no credit card required.

Claim 30-day Trial
See first-hand how CyberLab Control can improve your security posture with a free 30-day trial.
You’ll discover any hidden assets, map your entire external attack surface, crawl over 24 billion records for stolen credentials, and improve security awareness across your organisation.
No obligation, no credit card required.
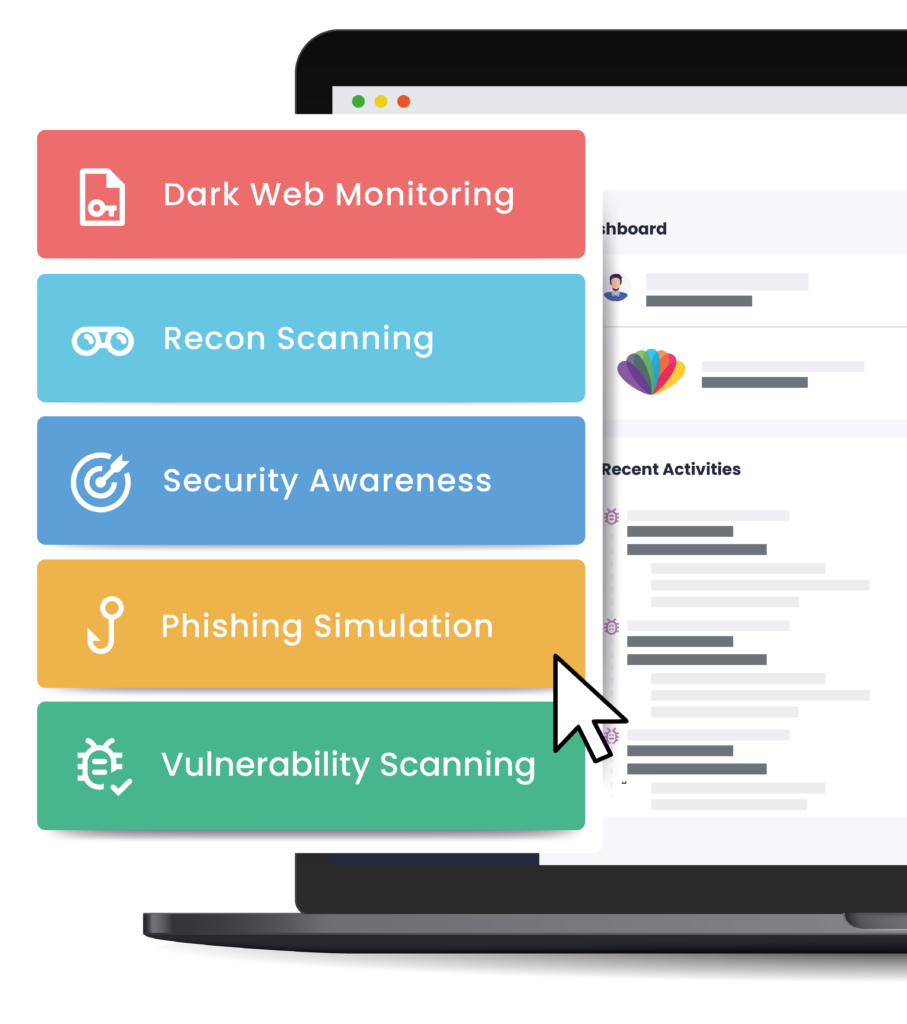
Featuring
Cloud Portal Access
No need to rely solely on PDF reports. Log in any time to see what we've found.
Seamless Integrations
Share pertinent cyber security data from the CyberLab portal via Slack and Teams with colleagues and partners.
Save Time & Effort
Say goodbye to the burden of managing user lists with auto-enrolment.
Automated Reports
Impress key stakeholders with executive summaries, exportable in PDF format.
AI-Powered Remediation Advice
Always receive the best most relevant, up-to-date advice with AI assistance.
Real Time Metrics
Instant access to all your key security metrics, displayed clearly on your dashboard.
Secure Data
Rest assured in the knowledge that your data is stored safely with CyberLab.
Always Available
Accessible anywhere and at any time to suit your busy schedule.
Speak With an Expert
Enter your details and one of our specialists will be in touch.
Whether you’re looking to implement basic cyber security best practice, improve your existing defences, or introduce a new system or solution, our team of expert consultants, engineers, and ethical hackers are here to help.
Our team specialise in creating bespoke security solutions and testing packages to improve and maintain your security posture.
We are 100% vendor agnostic and will only ever recommend the best products and solutions for your requirements.



