Zero Trust | Cyber Security Solutions
Protect.
Zero Trust Security Solutions
Keep your people, data, and systems secure with a Zero Trust approach to cyber security.
The Zero Trust approach means that your users, devices, and systems all start out with access to absolutely nothing. Then, as trust and confidence in user identity is built, additional levels of access are granted piece-by-piece, and only where necessary.

Why Implement Zero Trust?
Properly implemented, the Zero Trust model can help to solve a number of common business problems, and serve to reduce your overall risk level.
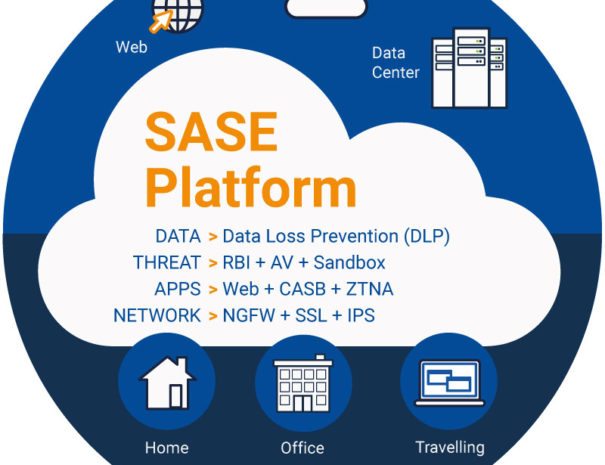
Different vendors approach the Zero Trust principle in different ways: some restrict access at the network layer, others at the data layer. We take the approach that best suits your organisation, systems, and policies.
Our team of experts are here to simplify the process of implementing Zero Trust to your organisation, and to help you build the solution that is right for you.
Reduce Attack Surface
Implementing a Zero Trust approach reduces the number of entry points by only allowing authorised users and systems to access your network.
Mitigate Insider Threats
Minimise the risk posed by insider threats, malicious or not, by ensuring users can only access precisely what they need to access.
Improve Data Security
Enhance the security of sensitive or business critical data since only those with a need-to-know are granted access.
Secure Vulnerable Areas
Provide peace of mind that vulnerable areas of your environment, such as devices running unsupported versions of operating system or applications that cannot be retired, are secure.
Zero Trust With CyberLab
Keep your data and systems secure by ensuring that only those people and systems who need access to perform their role are granted access.
No matter what systems you are using, our team of expert consultants are here to provide advice on the best approach to Zero Trust security for your organisation.
Detect.
The first step to implementing the Zero Trust framework is to gain an understanding of your current defences and Identity Access and Management systems.
Our online Posture Assessment tool is a simple way to gain a better idea of your cyber security posture. Based on the NCSC 10 Steps to Cyber Security, it only takes half an hour to complete and it will help you prioritise aspects of your security.
Our CHECK and CREST certified engineers will review any documented access policies and assess how well they have been implemented, whether it currently meets the standard of a Zero Trust model, and how it can be improved.
Protect.
Armed with the results of the preliminary tests, our team of expert consultants will design your Zero Trust solution to the bespoke requirements of your organisation, taking an approach that your team understand and can replicate for new systems in future.
Taking a staged appraoch, we will complement your VPN and Firewalls with Zero Trust Network Access (ZTNA) and apply identity-based segmentation to reduce your cyber risk.
By utilising our vendor partners and other enterprise-grade tools and applications, we will implement Zero Trust policies across your estate to ensure that your data is secure as possible.
Support.
We will equip your team with the knowledge and guidance necessary to utilise your new systems or programs effectively. Once your solution is in place, you can request support direct from the vendor, according to your service level agreement (SLA).
Additionally, you can take advantage of our years of experience supporting and maintaining the solutions with our range of Security Support services.
We'll look after the maintenance and configuration elements to ensure they are always in-line with industry best-practice, giving you both peace of mind and the time to focus on your other priorities.
Detect. Protect. Support.
Posture Assessment
Understand your security risks and how to fix them.
Take the first step to improving your cyber security posture, looking at ten key areas you and your organisation should focus on, backed by NCSC guidance.
Claim your free 30-minute guided posture assessment with a CyberLab expert.
Speak With an Expert
Enter your details and one of our specialists will be in touch.
Whether you’re looking to implement basic cyber security best practice, improve your existing defences, or introduce a new system or solution, our team of expert consultants, engineers, and ethical hackers are here to help.
Our team specialise in creating bespoke security solutions and testing packages to improve and maintain your security posture.
We are 100% vendor agnostic and will only ever recommend the best products and solutions for your requirements.