CyberLab Detect
Threat Detect
The early warning system for cyber security risks.
A combination of some of our most powerful security tools, Threat Detect provides you with all the information you need to act decisively and secure your environment.
This unique bundle provides unrivalled visibility across your entire attack surface; identifying weaknesses in your environment, discovering hidden and unmanaged assets, and understanding how much of your information is already in the hands of bad actors.
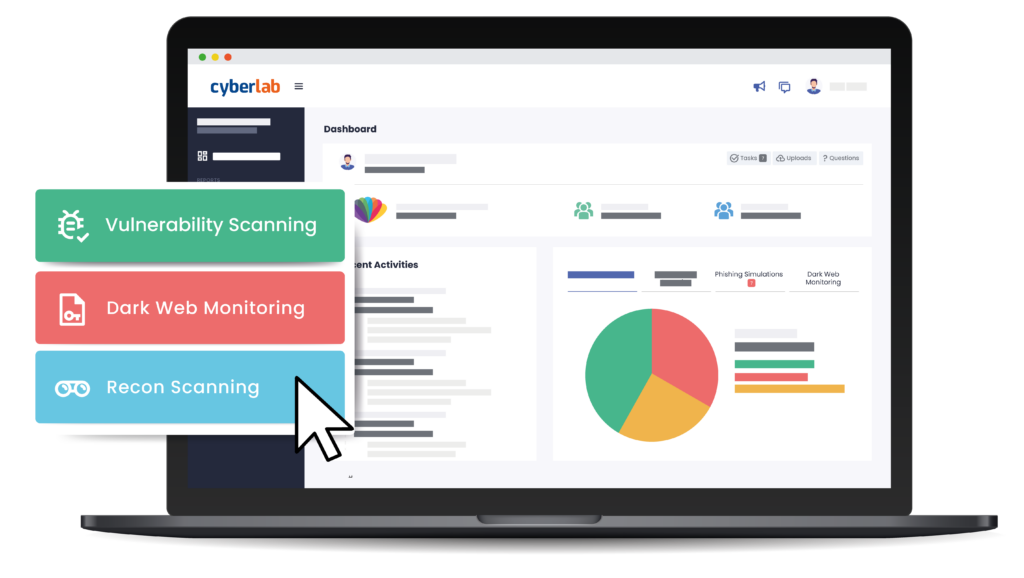
Uncover Your Entire Attack Surface
Identify every online asset and get the full picture of your attack surface
Keep Your Ear to the Ground
Monitor every corner of the internet for stolen business credentials
Stay a Step Ahead of Attackers
Manage security vulnerabilities before they can be exploited
Vigilance You Can Rely On
CyberLab Threat Detect surveys your assets for security vulnerabilities, monitors your attack surface, and scours the dark web for emerging risks.
Always on the lookout for threats to your organisation, Threat Detect provides proactive protection and real-time insights, ensuring that no threat goes unnoticed and no blind spots remain.
Whether it’s discovering unmanaged assets, identifying emerging vulnerabilities, or uncovering hidden dangers in the dark corners of the internet, Threat Detect is your first line of cyber defence.
1m+
Data breaches
identified
identified
15k+
Domains
monitored
10k+
Clients
protected
protected
Your attack surface is what a hacker sees when looking at your organisation from the outside. It’s every potential point of entry into your systems or network.
This includes, among other things –
• Vulnerabilities in software
• Open ports, services, or protocols
• Hardware components
• Your website, databases, and cloud assets
Threat Detect identifies exposed assets, open ports, breached credentials, emerging vulnerabilities, and other potential entry points in real time.
Exposed web assets, including admin panels, subdomains, login pages, expired certificates, open databases, APIs, are mapped to help you visualise your attack surface.
Threat Detect serves as an early warning system for vulnerabilities in your attack surface.
By continuously assessing your external-facing systems, you can proactively address security risks and reduce exposure to cyber threats.
The expert resolution advice within the portal helps you to resolve vulnerabilities and data breaches, and provides best practice to avoid cyber incidents.
"We searched the market extensively and found CyberLab had a fair price and an excellent understanding of our needs. This skill set and superior knowledge means they're the right partner for us."
– Lloyd Major, CEO, Halo
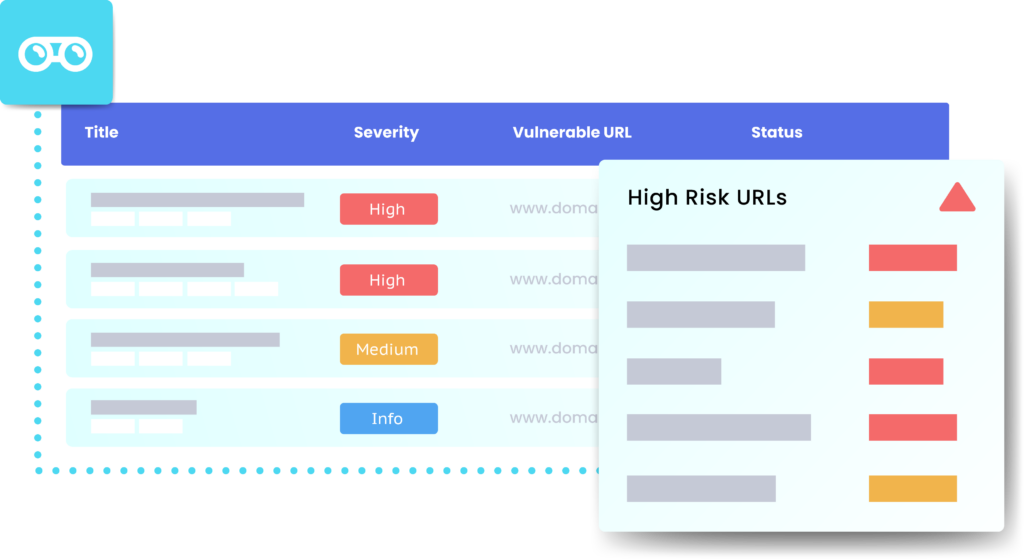
Unrivalled Visibility
See the Complete Picture
See every detail of your security environment within a couple of clicks.
Threat Detect identifies every online asset and helps you to understand exactly where it fits with the rest of your environment. New assets are automatically detected, and you’re notified whenever a change is detected.
Every detail of your online assets, data breaches, and identified vulnerabilities are available around-the-clock in our intuitive cloud portal.
Find & Fix Vulnerabilities Faster
Strengthen Security Posture
Threat Detect identifies your weak points in the same way an attacker would – by meticulously checking every online asset, application, web address, and internal device for vulnerabilities and configuration errors.
Timely alerts provide an early warning to emerging vulnerabilities, data breaches, and changes to your environment, allowing for faster response and resolution.
By assigning tasks via Slack and Teams directly from the portal, you can ensure that gaps in your security are plugged quickly and efficiently.
Map, Manage & Minimise
Reduce Attack Surface
Threat Detect maps and monitors your entire external attack surface – from public IP addresses and web URLs to internal devices and IT assets – for weaknesses such as outdated software, unpatched vulnerabilities, or misconfigured security settings.
Identify forgotten, shadow, or orphaned assets (old subdomains or forgotten cloud instances) that might be exposed externally, and assess the security posture of third-party services within your supply chain.
Armed with a complete digital asset inventory, you will see exactly where a real-life hacker might try to gain access, and what defences you need in place.
Uphold Security Audit Integrity
Protection Between Penetration Tests
Threat Detect provides a multi-layered approach to security, giving users visibility over potential threats and risks between penetration tests.
Unlike penetration testing, which occurs at a specific point in time, Threat Detect monitors for potential threats to your security throughout the year, alerting you to risks as they arise.
This proactive approach helps ensure that potential entry points in your attack surface are addressed quickly and exposed data is secured, reducing the likelihood of a successful attack.
Threat Detect Includes
Recon Scan
Recon Scan thinks like a hacker to uncover all your online assets.
Providing a complete picture of your attack surface, you can see where a real-life hacker could gain access.
Learn more about Recon Scan >
Attack Surface Monitoring (ASM) is the continual process of discovering, scanning, and assessing all external-facing assets, such as websites, APIs, and cloud services, to identify vulnerabilities and potential entry points. It helps reduce exposure and strengthen defences against cyber attacks.
Monitoring your attack surface helps identify exposed assets, vulnerabilities, and potential entry points in real time. By continuously assessing your external-facing systems, you can proactively address security risks and reduce exposure to cyber threats.
By identifying and addressing risks proactively, Recon Scan reduces your exposure to cyberattacks and strengthens your overall security posture.
Not monitoring your attack surface leaves you vulnerable to undetected threats, misconfigurations, and exposed assets. Attackers can exploit these weaknesses, leading to data breaches, financial losses, reputational damage, and compliance issues.
Not monitoring your attack surface leaves you vulnerable to undetected threats, misconfigurations, and exposed assets. Attackers can exploit these weaknesses, leading to data breaches, financial losses, reputational damage, and compliance issues.
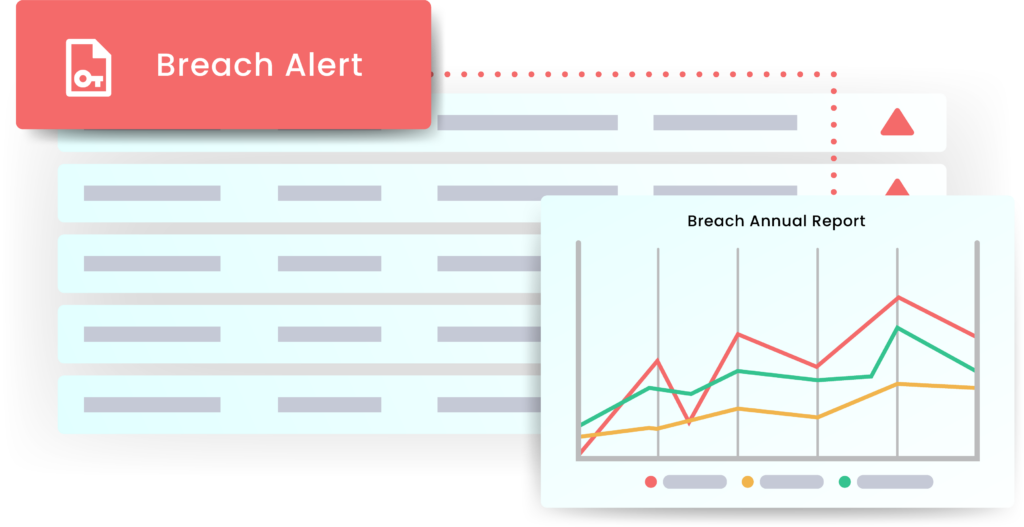
Dark Web Monitor
There are in excess of 24 billion stolen usernames and passwords for sale on the dark web, with more added daily.
Our advanced scanning software crawls the Dark Web for compromised business credentials.
Learn more about Dark Web Monitor >
The dark web is a hidden part of the internet where illegal activities, like selling stolen data and credentials, occur. Monitoring it for breached credentials helps identify if your sensitive information is exposed, enabling swift action to mitigate risks and protect your security.
Common ways data ends up on the dark web include:
• Hacking and Data Breaches
• Phishing and Social Engineering
• Ransomware Attacks
• Weak Credentials
• Insider Threats
Once exposed, this data can be used for identity theft, fraud, extortion, or further cyberattacks.
Having your data exposed on the dark web can have serious consequences.
Criminals may use your information to commit identity theft, fraud, or account takeovers.
Stolen credentials can be used to access your bank accounts, social media profiles, or sensitive business systems.
Exposed data can lead to financial losses, damage to reputation, and legal liabilities, especially where customer or employee data is involved.
The longer your data remains exposed, the greater the risk of it being used for malicious purposes.
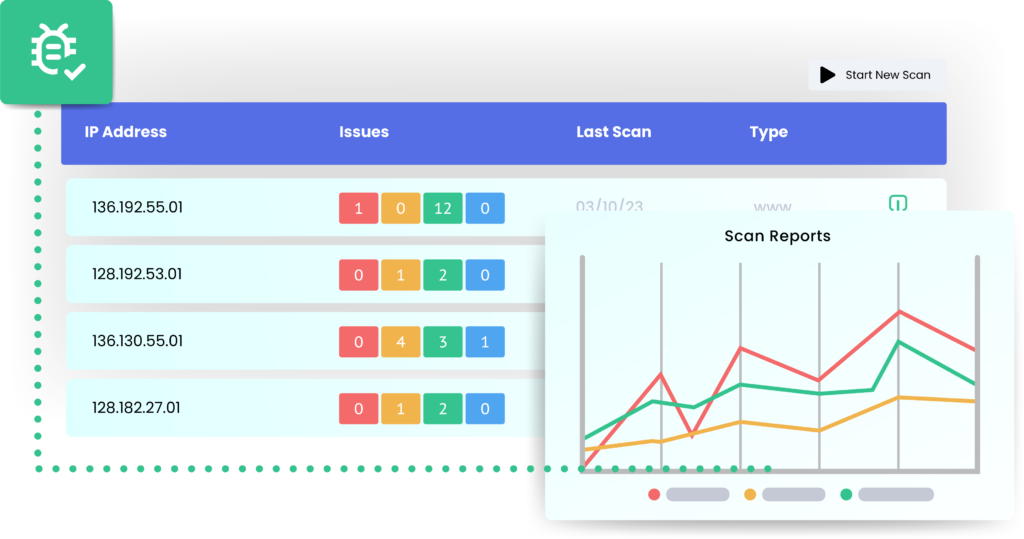
Vulnerability Scan
Unpatched vulnerabilities are the primary attack vector for successful ransomware attacks.
Vulnerability Scan keeps a constant eye on your environment and reports back on weaknesses, misconfigurations, and vulnerabilities.
Learn more about vulnerability scanning >
Scanning for vulnerabilities helps identify weaknesses in your systems before attackers can exploit them. It allows you to patch security flaws, reduce risks, and strengthen your defences, ensuring your network remains secure from potential cyber threats.
A vulnerability scan identifies weaknesses in software, misconfigurations, outdated systems, exposed services, unpatched security flaws, and other potential entry points.
It detects and alerts you to risks like open ports, insecure protocols, and weak passwords, helping to prevent cyberattacks before they happen.
Vulnerability scanning keeps you safe by automating the detection of security gaps across your systems. It helps prioritise risks, allowing you to fix critical issues quickly, ensuring compliance, and reducing the chance of exploitation by attackers.
Threat Detect
Claim 30-day Trial
See first-hand how Threat Detect can improve your security posture with a free 30-day trial.
You’ll discover any hidden assets, map your entire external attack surface, and crawl over 24 billion records for your stolen credentials.
No obligation, no credit card required.



