Cyber Security Challenges Within The Public Sector James Ambrose, Head of Public Sector Sales, reviews the threat hunting requirement part of the recently published Government Cyber Security Strategy. He covers: The UK is one of the most digitally advanced countries, … Read More
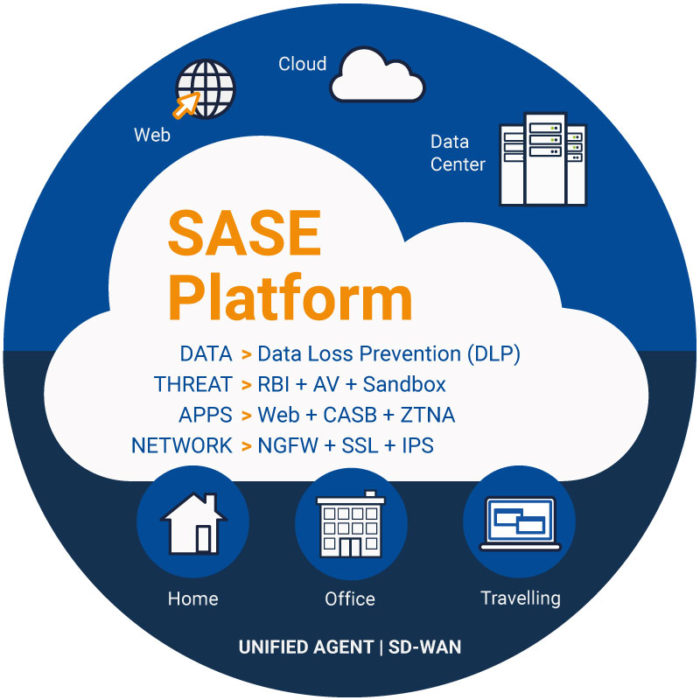
Protect Your Data with SASE
What is SASE and How Does it Work Secure Access Service Edge (SASE) Explained Gavin Wood, CyberLab CEO, explains the emerging cyber security concept SASE (Secure Access Service Edge). He covers: What is Secure Access Service Edge (SASE) SASE Components … Read More

Finding Your Cyber Security Weaknesses
What is a Vulnerability Assessment & What Does it Do A Guide to Vulnerability Assessments Adam Gleeson, Vendor Alliance Manager at CyberLab, offers insight into how cyber security vulnerability assessments can help businesses protect and improve their systems. He covers: … Read More

Hybrid Warfare and Cyber Attacks
Hybrid Warfare and Cyber Attacks Steve Clarke, Head of Penetration Testing, reviews the most recent news on cyber attacks, hybrid warfare and the conflict in Ukraine. He covers: The Conflict in Ukraine and Cyber Warfare Both sides in this conflict … Read More

Quick Wins to be Cyber Secure
Quick Wins to be Cyber Secure https://youtu.be/vy_4yneHEsc?feature=shared Jack Smallpage, Information Security Officer at CyberLab, explains five simple things you can do to protect your business and improve your cyber security. Cyber security is a broad subject with hundreds of … Read More
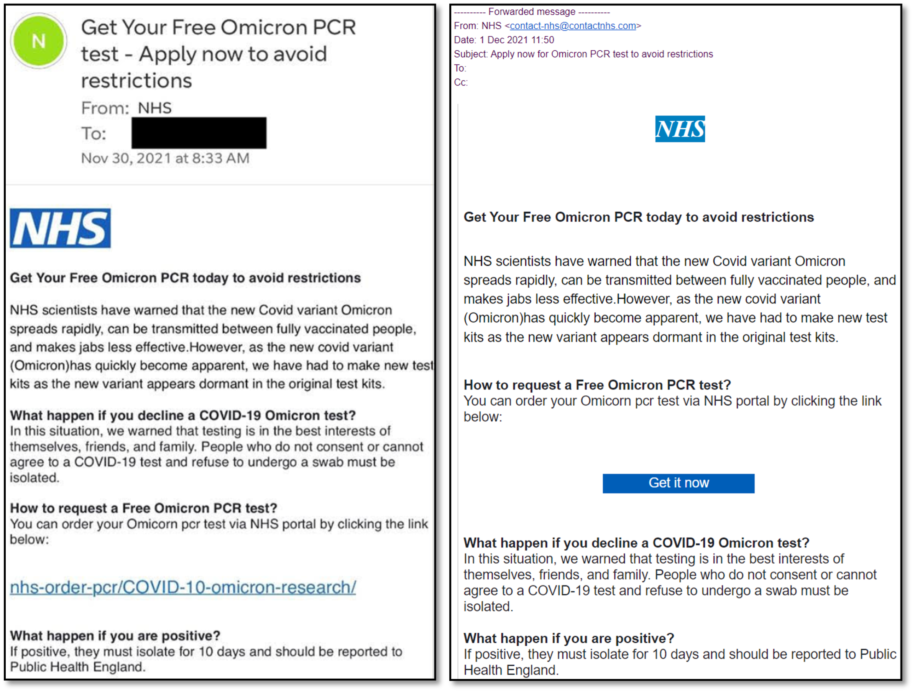
Warning: Omicron Variant PCR Phishing Emails
Warning: Omicron Variant PCR Phishing Emails There has been a sudden increase in the number of phishing emails being sent out in an attempt to cash in on the anxiety and confusion regarding the new Omicron Covid variant. The emails … Read More

Your CREST Accredited Penetration Test Report
Your CREST Accredited Penetration Test Report Gavin Wood, CEO at CyberLab, uncovers what a Penetration Test report should provide. Penetration Testing or Pen Testing is a crucial tool in your IT security toolbox. It provides a method for gaining assurance … Read More

IKEA hit by reply-chain email attack
IKEA hit by reply-chain email attack IKEA is fighting the consequences of a cyber attack which started on its email platform, where an adversary used legitimate email addresses of employees to spread malicious attachments to other IKEA employees. The attacks … Read More

Vulnerability Assessment versus Penetration Test
Vulnerability Assessment versus Penetration Test What’s the difference? Gavin Wood, CEO at CyberLab, explains the difference between Vulnerability Assessment and Penetration Testing and their applications. Vulnerability Assessments (VAs) are usually seen as a lesser service when compared to a Penetration … Read More

Prevention v Cure: Introduction to Pen Testing
Prevention v Cure: Introduction to Pen Testing CyberLab CEO Gavin Wood explains what penetration testing is and why diagnosing vulnerabilities earlier can save you money. What is Penetration Testing? Prevention v Cure? Before I answer that I think I will … Read More
