IKEA hit by reply-chain email attack
IKEA is fighting the consequences of a cyber attack which started on its email platform, where an adversary used legitimate email addresses of employees to spread malicious attachments to other IKEA employees. The attacks are believed to have involved on-premise Microsoft Exchange servers.
What is a reply-chain attack?
Hijacking an email reply chain begins with an email account takeover. Either through an earlier compromise or techniques such as credential stuffing and password-spraying, hackers gain access to one or more email accounts and then begin monitoring conversation threads for opportunities to send malware or poisoned links to one or more of the participants in an ongoing chain of correspondence.
With emails coming from what are considered ‘known sources’ it is easier to bypass employee’s sanity checks and not apply the same level of caution as external and unknown senders.
IKEA warn their employees
“This means that the attack can come via email from someone that you work with, from any external organisation, and as reply to an already ongoing conversation. It is therefore difficult to detect, for which we ask you to be extra cautious.”
An example of the phishing email sent to IKEA employees
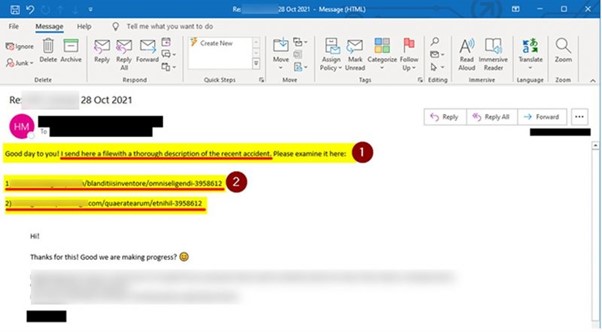
What can you do to protect your organisation from reply-chain email attacks?
Because a reply-chain attack is the result of an account compromise, one of the best ways to prevent this form of cyber attack is to ensure that Multi Factor Authentication (MFA) is enabled on all mailboxes along with strong passwords.
A reply-chain cyber attack is reliant on a user clicking on a malicious link to spread malware. Educate your users that such cyber attacks exist and ask them to be vigilant of internal as well as external senders.
In addition, encourage users to reach out to a colleague using Teams or on the phone to confirm whether the email was indeed sent from them.
It is yet to become clear whether IKEA’s cyber attack was the result of unpatched Exchange servers allowing mailboxes to be compromised but ensuring that all devices are fully patched should be an essential part of every cyber security strategy.
CyberLab Control | Cyber Security as a Service
Free 14-day Trial
Experience the beneifts of an all-in-one cyber security portal with a free 14 day trial.
No obligation, no credit card required.

Facebook Data Breach Investigation

