In The News: Follina Windows Zero-Day, DDos and Citrix Attacks, Cisco Lifecycle Reminder
Jack Smallpage, Information Security Officer at CyberLab, reviews the latest cyber security news and advises how to protect your data. He covers:
-
- Follina Windows Zero-Day
-
- Cloudflare’s defends a record DDos Attack
-
- Atlassian’s Confluence Zero-Day
-
- Citrix attackers can reset your admin!
-
- Cisco reminds us to check our lifecycles
-
- Microsoft Enforcing better Security Defaults
-
- Book Your Consultation
Welcome to the second issue of our Cyber Month in Review series. I’ve summarised for you some of June’s highlights in this 5-minute read to help you be more cyber aware.
Follina Windows Zero-Day
Starting with a major vulnerability which has been running its course this month, the “Follina” zero-day (tracked as CVE-2022-30190) is a vulnerability in the ‘Microsoft Support Diagnostic Tool’ (MSDT). This dangerous flaw is currently being exploited globally, including by the ever-worrying APT (Advanced Persistent Threat) actors. The exploit allows attackers to execute malicious PowerShell commands via MSDT through crafted applications such as Word. To make matters worse, the exploit works by opening or even just previewing the document. It doesn’t need macro code enabled to run the scripts, allowing the attacker to then install programs, view, change, or delete data, or create new accounts in the context allowed by the user’s rights. This macro-less nature makes the attack particularly attributable to phishing attacks – so be aware!
What Should I do
Thankfully this was patched in the June 2022 deployment, so make sure you have rolled this out to your business for remediation. If you cannot deploy this patch, however, you can disable the MSDT URL protocol as a workaround to mitigate the threat as detailed here: Guidance for CVE-2022-30190 Microsoft Support Diagnostic Tool Vulnerability – Microsoft Security Response Center
Cloudflare’s defends a record DDos Attack
At the start of this month, Cloudflare stated that they had mitigated a 26 million request per second distributed denial of service (DDos) attack, being the largest HTTPS DDos attack detected to date! The attack purportedly utilised a ‘less is more’ approach with virtual machines and powerful servers being used to generate the attack rather than weaker but more numerous Internet of Things (IoT) devices. Read more on this here: Cloudflare mitigates 26 million request per second DDoS attack
What Should I do
Whilst this is not aimed at endorsing Cloudflare’s DDos solution, it is an important reminder that in a world of ransomware, other attacks such as DDos continue and advance in power and complexity. Make sure your business has planned for these types of attacks in your business continuity plan and have measures in place (whatever they may be). You can find guidance on making a DoS plan on the NCSC site here: Preparing for denial of service (DoS) attacks – NCSC.GOV.UK
Atlassian’s Confluence Zero-Day
Attackers have been actively exploiting a Zero-day in Atlassian Confluence this month. Tracked as CVE-2022-26134, the unauthenticated remote code execution (RCE) exploit allows the unauthenticated attacker to create new admin accounts and execute commands to compromise and otherwise takeover the affected server in Confluence Data Centre and Server (not including Atlassian Cloud sites).
What Should I do
Atlassian have now released the patch for this vulnerability. If you are affected and have not done so already, get it patched as soon as possible! Released versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1 contain a fix for this issue. More detail on this patch and mitigation options can be found here: Confluence Security Advisory 2022-06-02 | Confluence Data Center and Server 7.18 | Atlassian Documentation
Citrix attackers can reset your admin!
Citrix have warned customers this month to deploy security updates with particular focus on a critical ‘Improper Access Control’ vulnerability regarding the Citrix Application Delivery Management (ADM). Citrix ADM is a web-based solution which provides admins with a cloud-based console for managing on-prem and cloud Citrix deployments.
Successful exploitation of this vulnerability would allow an unauthenticated, remote attacker to corrupt the system and reset the admin password at the next device reboot, allowing an attacker with ssh access to connect with the admin credentials after the reboot.
What Should I do
As with others, it is vital that vulnerabilities such as this are patched as soon as possible to reduce the likelihood of compromise. If you use Citrix ADM within your business (Citrix ADM 13.1 before 13.1-21.53 or Citrix ADM 13.0 before 13.0-85.19), make sure to apply the patch offered by Citrix – more details can be found here: Citrix Application Delivery Management Security Bulletin for CVE-2022-27511 and CVE-2022-27512
Cisco reminds us to check our lifecycles
When was the last time you checked the lifecycle of your software? More specifically, to this entry, when was the last time you checked the end of support/life date of your hardware? A critical vulnerability has been found in the web-based management interface of Cisco Small Business routers. Exploiting this vulnerability could allow an unauthenticated and remote attacker to execute commands with root-level privilege.
In particular, the vulnerability affects the following small business RV series routers:
-
- RV110W Wireless-N VPN Firewall
-
- RV130 VPN Router
-
- RV130W Wireless-N Multifunction VPN Router
-
- RV215W Wireless-N VPN Router
What Should I do
Of more importance here, is that this vulnerability has identified no workarounds (though it only affects devices with the web-based remote management interface enabled on WAN connections), and Cisco do not intend to release a patch. Instead, they warn customers that the affected devices are end of life and customers should instead upgrade to newer models following best security practice. More details of this can be found here: Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers Remote Command Execution and Denial of Service Vulnerability
Microsoft Enforcing better Security Defaults
So, with all this talk of vulnerabilities and attackers, Microsoft have jumped in to give us a hand defending our business. Announcing that it has already begun the rollout of security defaults on all existing Azure AD tenants, the security defaults introduced in October 2019 will be enabled automatically moving forward for all existing Microsoft customers. This will help protect an additional 60 million accounts, protecting your network and reducing the strain on your IT teams with features such as conditional access, identity protection, and MFA.
What Should I do
You will likely already been notified, but if you haven’t, your global administrators will be given the option to enable the defaults with an alert like the image below or “snooze” the enforcement for 14 days, where it will then be toggled on automatically.
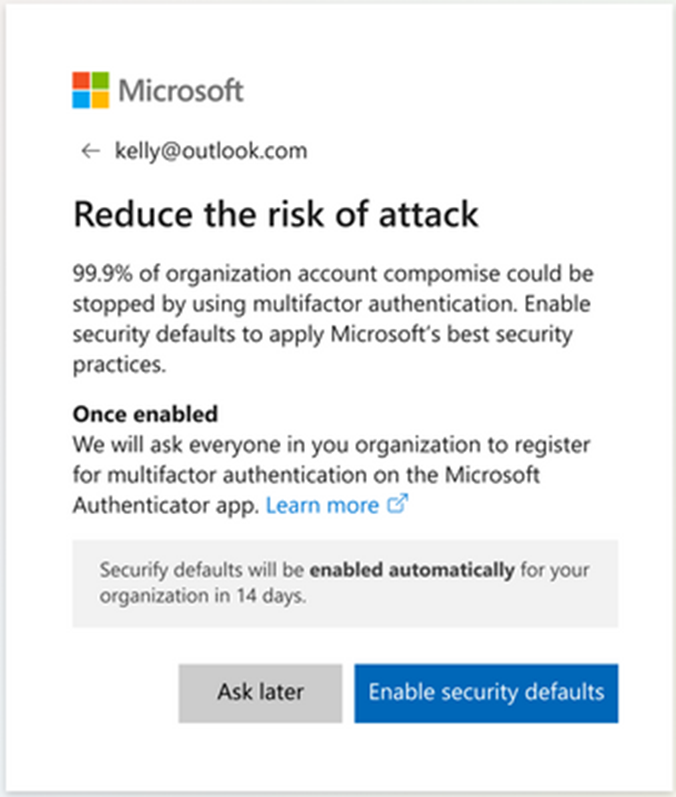
Make sure you go through these settings and ensure they fit your business’s requirements and risk appetite. If you need help understanding these settings and configurations, CyberLab is on hand to help you out should you need it! More details can be found here: Raising the Baseline Security for all Organizations in the World – Microsoft Tech Community
“We are confident that our users cannot be compromised from outside the organisation – that was the biggest concern we had at the beginning of our (Microsoft) path. It gives myself as the Head of IT and our board the peace of mind that our accounts are secure.”
Head of IT, MDL Marinas
Conclusion
With the Follina exploit causing a panic in the early weeks and other vulnerabilities being detected and exploited across the board, this week has shown both the red team’s attempts to compromise and the blue teams’ achievements in defending our global interest in security. As always, it is important to reiterate that this article has not included ALL security news or vulnerabilities disclosed this month, and others such as Microsoft’s Patch Tuesday’s other fixes, Internet Explorer’s retirement, Android’s critical security update, and Gitlab’s Account Takeover flaw (patched) are just honourable mentions as examples of other updates you should be aware of and research.
If you have been caught off-guard by some of this month’s developments, have a look at your security processes and see what changes you can make to ensure you don’t get caught out in the future. Just 20 minutes of research each day can help you keep on top of the major security trends and alerts, which help protect your business and keep you cyber aware! If you have any more questions or worries, please do not hesitate to get in touch and see what CyberLab can do to help you and your security posture.
Detect. Protect. Support.
Posture Assessment
Understand your security risks and how to fix them.
Take the first step to improving your cyber security posture, looking at ten key areas you and your organisation should focus on, backed by NCSC guidance.
Claim your free 30-minute guided posture assessment with a CyberLab expert.

Cyber Month in Review March 2023


Leave a Reply
You must be logged in to post a comment.