Security for Small and Medium-Sized Enterprises (SMEs)
Adam Gleeson, Cyber Security Vendor Alliance Manager, reviews the five key essential functions small and medium-sized organisations require to be cyber secure. He covers:
- Traditional Anti-malware Protection is No Longer Enough
- Patching: Keep Your Systems Up To Date
- Security Awareness Training is Crucial
- The Modern Firewalls
- Regular Testing
- How a Ransomware Phishing Attack Works
- Recover from a cyber attack
- Introduction to Cyber Disaster Recovery
- Creating Your Disaster Recovery Plan
- Regular Testing
Cyber security Nirvana is the state you reach when you are 99.9% confident in your cyber security protections. This was, at one point, many years ago, something that was actually achievable. These days? Not so much.
The relentless and somewhat unique ways in which our technology, work life, digital tools and personal lives continue to evolve and advance means cyber security Nirvana is now one of those things you will never ultimately attain.
However, you can build your cyber security strategy in such a way that you can have confidence you are doing everything you can whilst equipping yourself for whatever new threats appear on the horizon. Small and Medium-sized organisations (SMEs) need to focus on five essential functions I will describe below.
Traditional anti-malware protection is no longer enough
I see a range of approaches to anti-malware. Attitudes range from “It’s something I know I need to have, but anything will do” to “I want to have the best I can, but it needs to be affordable”. The latter is the approach that you should adopt.
The antivirus (or the modern term, endpoint protection) you run on all your users’ computers is a critical line of defence. It can spot things happening that may not be visible to the person using the computer. Your endpoint security/ antivirus can mean the difference between spotting a virus or hacker’s nefarious activity and you being another ransomware victim.
In this regard, you need to be looking at the best you can afford, and you need to be able to afford a next-generation solution. The traditional approach of the scanner having a ‘naughty list’ of known software threats is no longer sufficient. New threats emerge hourly, and the ‘naughty list’ approach can’t keep up.
This is where the next-generation solutions come in. The new approach to is to look at process and software behaviours. While we may not be able to keep up with the latest emerging threats, 99.9% of them behave in a known manner. That is, they may be a new version or type of danger, but the nature of what they are there to do hasn’t changed. By monitoring for the key behaviours associated with these threats, we can detect them without needing to know about them beforehand, providing us with a constantly up-to-date defence mechanism.

Patching: Keep your systems up to date
The software we run shifts and constantly changes. As with external software threats, the landscape we face from internal vulnerabilities needs addressing through effective software update (or patch) management.
New features enhance functionality or improve the software to make our jobs easier. However, with any new software code, there is a potential for bugs – most are harmless, but some represent significant security risks. Historically these bugs often went unnoticed. Nowadays, most software vendors offer ‘bug bounties’, rewarding anyone who can identify a bug/flaw in the software. Unfortunately, attackers often can exploit these bugs to install malicious software.
Security flaws in new software are uncovered and publicised quickly – both to the software vendor and the internet at large – meaning that it is more important than ever to ensure that your software is kept up to date to ensure that this easy attack vector does not exist.
Security awareness training is crucial
Your users can be the weakest link in your cyber security defence, OR they can be your greatest asset. Which end of the scale they sit at depends entirely on how well they are trained in security best practices.
Last year the vast majority of cyber attacks launched against UK businesses were initiated with a phishing attack via email. Had the users that clicked on those emails been more aware of what to look for, most of those attacks could have been easily prevented.
Many different solutions are available today that provide phishing awareness and simulations. You can train your users and help them understand where they made mistakes, so they can put into practice what they are being taught and learn what to look for.
The modern firewalls
The concept of firewalls is not new. We’ve had them for decades, but the task the firewall must fulfil has become more challenging in line with the other increases in technological complexity.
Traditional rule-based firewalls still work to an extent. However, with the rapid changes in how we operate, management of the rules can become burdensome. If not kept up to date, they can cease to be effective defences.
Many businesses are now adopting ‘next-generation’ (that phrase again) firewalls. These will feature far more robust defensive protection and internal and external network traffic analysis to pick up on potentially malicious behaviour or software indicators. Their ability to dynamically accommodate new application requirements of the users can also be a key factor. For example, allowing applications firewall access from specific software vendors (e.g., Microsoft) may alleviate some of the work required of your helpdesk as manual rules will not need to be configured for each application instance.
Regular Testing
Finally, having great security products deployed to protect your business and users is fantastic, but if those solutions are not configured correctly, they cease to be an effective defence. For this reason, regular testing of your systems and your users is an essential activity to perform. Would you prefer to find out your AV isn’t up to scratch when it’s ‘no-harm-done’ or when your business is in crisis mode?
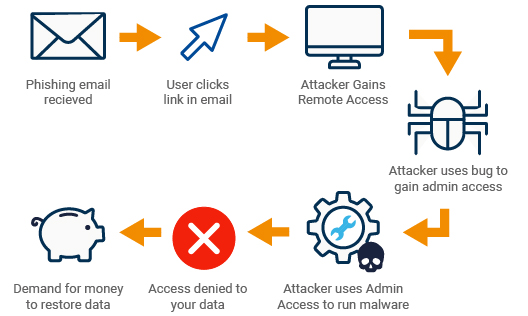
How a ransomware phishing attack works
To add context to some of the points I have raised above, I have illustrated just how easy it can be to run afoul of ransomware. To be clear, this is not the only method of attack that can lead to an infection, but it is one of the most common. A typical example would be phishing attacks that lead to ransomware infection.
Introduction to Cyber Disaster Recovery
Disaster Recovery involves policies, tools and procedures to cover your organisation’s plan and ability to respond to a disaster and recover critical business infrastructure.
In the film Jurassic Park, computer programmer Dennis Nedry deliberately disables and locks people out of the parks systems (almost like an insider threat actor deploying ransomware!). In the film, this causes various prehistoric carnivores to run amok, snacking on the protagonists. To restore their systems, it’s a simple case (apart from the dinosaur attack) of restarting the systems (switch it off and on again!) and boom, all the systems come back online, and they can escape. If only Disaster Recovery was that simple!
Disaster Recovery is one of the parts of ITSM (Information Technology Service Management) that I would include in getting the basics right (see also: patching, antimalware, etc). It also plays a vital part in your overall security strategy.
I have discussed defence in depth in previous blogs, and at the very heart of that strategy is having a good DR plan. If your layers of defence fail to protect you, being able to restore your systems quickly and efficiently is crucial to your business’s survival. Think about how long you can go without your critical systems before reputation or revenue is affected.
An example of how disastrous a DR event can be even months after it happens is the attack that affected Gloucester Council last year. As reported recently by the BBC, the Council’s IT systems are still not fully back up and running. That’s nearly ten months of downtime!
So in the aftermath of a cyber-attack or any event that caused widespread destruction to your IT systems, you will need a DR plan to get you back on track.

Creating Your Disaster Recovery Plan
So, what makes a good DR plan? There are several steps you should follow when creating your DR plan:
Review your infrastructure and make sure you know your estate. If you can’t see it, you can’t manage or recover it in the event of failure.
Complete an impact assessment for each system. What is the impact on your business of losing access to that system or its data?
Identify business-critical systems and prioritise these first.
Work out what your Recovery Time Objectives (RTO) need to be. This is the amount of elapsed time your business can survive without access to these systems. There will be different RTOs for different systems depending on criticality/business impact.
Choose an appropriate DR technology. From real-time replication of block-level data to a remote site through to once-a-week tape backup kept securely offsite, many options exist. For each system, you will need the appropriate technology to ensure you can meet your RTOs.
“We could not have picked a better time to implement the changes from a standard in-situ server to a cloud-based solution. Our enforced homeworking would be considerably more difficult without this. Like all IT projects, there are always a few challenges, but these were tackled with knowledge and enthusiasm and quickly sorted out. The aftercare is great and we are looking forward to discussing further potential improvements to our systems.”
– Simon Fielding, Finance Director, The Kay Group
Ensure you have the right policies/procedures to review and regularly amend the DR plan.
Most importantly, have a plan and test it.
-
- What is the agreed trigger point for a DR plan to be implemented?
-
- What is the process for restoring the systems?
-
- Who will trigger the restore?
-
- How will you bring the system back into service?
-
- Who communicates this to the business?
All this needs to be documented and kept somewhere accessible. Not on a system where it could be inaccessible in a DR event!
Regular Testing
Once you have the plan, regular testing is essential, and when I say testing, I mean testing properly. Just reviewing backup jobs and checking replication status is not enough. Testing is the only surefire way to ensure that in the event of a disaster, you stand a chance of being able to recover.
The first few times you test the plan, you may fail to be able to recover, but this is not a failure. You will only work out the issues in your plan by trying it out, and each time your plan and procedures will improve, giving you that fighting chance of fully recovering.
I haven’t covered business continuity (BC) in this article. That is a much broader conversation in which DR features. A well-tested DR plan will be crucial if you are working on a BC strategy.
Please reach out if you want to talk about protecting your data from ransomware attacks or support with your business continuity and disaster recovery plans.
Detect. Protect. Support.
Posture Assessment
Understand your security risks and how to fix them.
Take the first step to improving your cyber security posture, looking at ten key areas you and your organisation should focus on, backed by NCSC guidance.
Claim your free 30-minute guided posture assessment with a CyberLab expert.

Cyber Month in Review November 2022


Leave a Reply
You must be logged in to post a comment.