Delinea | Our Vendor Partners
Our Vendor Partner
Delinea
Delinea ensures data privacy and confidentiality, whether in transit or at rest. Securely implement and enforce organisational access policies, and bolster your first-line-of-defence against malware, phishing attacks, and other cyber threats.

Safeguard Sensitive Systems with CyberLab and Delinea
Mimecast makes email safer for your organisation with solutions that secure, preserve, and continue the flow of information, protect against email-borne threats, and ensure secure communication with comprehensive threat detection and prevention mechanisms.
Reduce Your Risk
A smaller attack surface gives threats less to work with.
Protect Privileged Accounts
Secure and manage privileged accounts that could be abused.
Seamless Security
Scalable, customisable, and strong enough to secure any system.
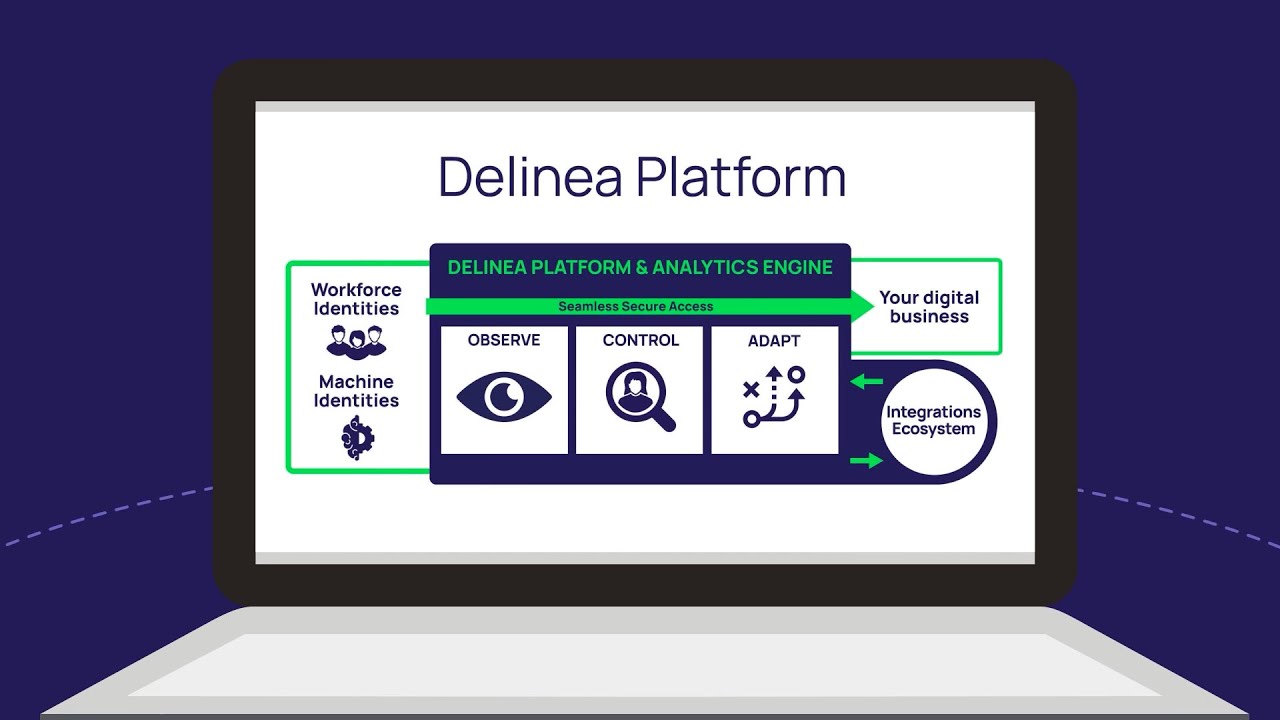
Seamlessly Extend Privileged Access Management with Delinea
Learn why Delinea Secret Server customers are extending Privileged Access Management (PAM) to protect hybrid infrastructures, meet compliance requirements, and enable secure remote access.
Detect. Protect. Support.
Posture Assessment
Understand your security risks and how to fix them.
Take the first step to improving your cyber security posture, looking at ten key areas you and your organisation should focus on, backed by NCSC guidance.
Claim your free 30-minute guided posture assessment with a CyberLab expert.
Speak With an Expert
Enter your details and one of our specialists will be in touch.
Whether you’re looking to implement basic cyber security best practice, improve your existing defences, or introduce a new system or solution, our team of expert consultants, engineers, and ethical hackers are here to help.
Our team specialise in creating bespoke security solutions and testing packages to improve and maintain your security posture.
We are 100% vendor agnostic and will only ever recommend the best products and solutions for your requirements.



