What is SASE and How Does it Work
Secure Access Service Edge (SASE) Explained
Gavin Wood, CyberLab CEO, explains the emerging cyber security concept SASE (Secure Access Service Edge). He covers:
-
- What is Secure Access Service Edge (SASE)
-
- SASE Components
-
- SASE v SSE (Security Service Edge)
-
- Why do I need SASE or SSE?
-
- Book your Free consultation
I first seriously encountered the term SASE in The Future of Networking Security Is in the Cloud in November 2020. It’s an excellent document, and even though it is almost 3 years old, it is still relevant today. With accelerated global changes in working practices driven by the global COVID pandemic, SASE has helped shape the security infrastructure and services we consume.
So, what is SASE?
Secure Access Service Edge (pronounced “sassi” or “sassy”)
SASE combines network security functions with WAN capabilities (i.e., SD-WAN) to support organisations’ dynamic secure access needs.
A secure access service edge (SASE) is a technology used to deliver a wide area network (WAN), via SDWAN technologies and security controls, primarily delivered in the as-a-service model, directly to the source of connection. That source could be a user, device, branch office, or IoT rather than a data centre.
As the traditional network topology changes from a data centric model where the core of your services are deployed and managed centrally in a ringfenced environment to the much more flexible working environment with dispersed hybrid workforces, SASE becomes increasingly important to ensure security can be maintained, but also user experience is not compromised.
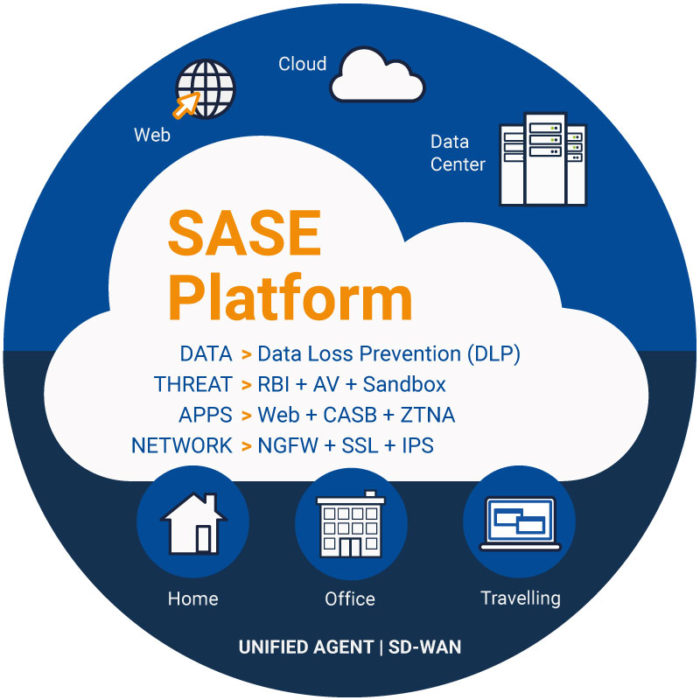
Secure Access Service Edge (SASE) Components
Software-defined Wide Area Network (SD-WAN)
Software-defined wide area network or SD-WAN is a set of technologies that allow companies to build a lower cost, higher capacity WAN infrastructure using a mixture of protocols such as MPLS, DSL, VPN. The “Software” element determines the best route for the traffic based on criteria. For example, services requiring performance guarantees are routed over private MPLS connections, whereas other traffic is routed via DSL internet connections.
Cloud Access Security Brokers (CASB)
An on-premises or cloud-based security policy enforcement points are placed between cloud service consumers and providers to combine and interject enterprise security policies as the cloud-based resources are accessed. CASBs consolidate multiple types of security policy enforcement. Example security policies include authentication, single sign-on, authorisation, credential mapping, device profiling, encryption, tokenisation, logging, alerting, malware detection/prevention etc.
Firewall as a Service (FWaaS)
FWaaS is a firewall offered as a cloud service rather than on-premises as software or hardware. Most FWaaS providers offer next-generation firewall capabilities. Typically, an entire organisation is connected to a single FWaaS cloud with no requirement for maintaining its own firewall infrastructure. SASE combines edge FWaaS with other security functions and SD-WAN.
Zero Trust Network Access (ZTNA)
The zero-trust security model, ZTNA, sometimes known as perimeter-less security, describes an approach to designing and implementing IT systems. The main concept behind the zero-trust security model is “never trust, always verify.” This means that devices should not be trusted by default, even if they are connected to a permissioned network such as a corporate LAN and were previously verified.
Secure Web Gateway (SWG)
Secure Web Gateway (SWG) solutions protect web-surfing PCs from infection and enforce company policies. The solution filters unwanted software/malware from user-initiated Web/Internet traffic and enforces corporate and regulatory policy compliance. These gateways must, at a minimum, include URL filtering, malicious-code detection and filtering, and application controls for popular Web-based applications.
SASE v SSE: What is Security Service Edge?
Security Service Edge (SSE), is the security component of SASE that brings all of the security elements – ZTNA, CASB, SWG, and FWaaS – together without the WAN part. These services can be applied across separate WAN technologies.

Why do I need SASE or SSE?
The truth is you probably have some of these elements in your network already. With the rapid shift to hybrid working, businesses have had to adapt and change their infrastructure to continue to work securely. The piecemeal deployments of some or all of the SASE elements are typical. What organisations are missing are the plans to continue to adopt the SASE elements in a structured and cohesive way. Plus, they should have a plan to ensure these elements come from as few vendors as possible, ensuring that security management is efficient.
SASE is not based on hardware, IP addresses that change frequently or devices that move location multiple times throughout the day. Instead, it is based on identity, which is key to tracking security events. Applying policies to identities ensures a consistent set of controls for that profile no matter what service is being accessed from whatever location.
SASE is also scalable. Shifting away from the data centre centric model requires more access points to a network, but adding hardware and circuits to an infrastructure to support our hybrid workforce is expensive and rigid. In a world where connectivity is managed no matter the connection type and security is maintained across that connection, SASE gives us that business agility that we need.
Our services and technology partners like Cisco and Forcepoint allow us to take our customers on a security journey to a complete modern secure architecture and make it easy to work securely from anywhere.
Detect. Protect. Support.
Posture Assessment
Understand your security risks and how to fix them.
Take the first step to improving your cyber security posture, looking at ten key areas you and your organisation should focus on, backed by NCSC guidance.

Cyber Month in Review December 2022

Leave a Reply
You must be logged in to post a comment.