Cyber Essentials - Montpellier Question Set Released
On 23rd January, the NCSC publishes an updated set of requirements, version 3.1 for the Cyber Essentials scheme which will come into force on the 24th April 2023. The ‘Montpellier’ question set will replace Evendine. Additionally, the grace periods for some of the requirements from the 2022 update will end on 24th April.
Any assessments that began before 24th April, will continue to use the requirements version 3.0 with the Evendine question set. This includes any assessment accounts created before 24th April.
This year, the changes to the scheme are as follows:
1. The definition of ‘software’ has been updated to clarify where firmware is in scope
-
- Software includes operating systems, commercial off-the-shelf applications, plugins, interpreters, scripts, libraries, network software and firewall and router firmware.
Why the change?
Firewall and router firmware is the operating system of those devices. As firewalls and routers are key security devices, their operating systems and whether they are kept up to date is extremely important from a security perspective.
And another thing…
Cyber Essentials will require that all applicants list their laptops, desktops, servers, computers, tablets and mobile phones, with details of the make and operating system. However, when it comes to firewalls and routers, the applicant will only be asked to list make and model, but not the specific version of the firmware. By asking for the make and model on these devices, the Assessor will be able to determine if the devices is still receiving security updates to the firmware.
2. Asset management is important in Cyber Essentials
In a similar vein to backing up data, asset management isn’t a specific Cyber Essentials control, but it is a highly recommended core security function. By including this subject in the Cyber Essentials requirements, the importance of good asset management is being emphasised.
Why ?
The requirements clarify that asset management doesn’t mean making lists or databases that are never used, it means creating, establishing and maintaining authoritative and accurate information about your assets that enables both day-to-day operations and efficient decision making when you need it. Security experts often refer to asset management as a fundamental cyber hygiene practice that can help an organisation meet all of the Cyber Essentials five controls. Many major security incidents are caused by organisations having assets which are still connected to the network when that organisation is not aware the asset is still active. Effective asset management will help track and control devices as they’re introduced into your business.
The NCSC has comprehensive guidance for organisations on asset management.
3. A link to the NCSC’s BYOD guidance added for information
For further information and advice on the use of BYOD, please see the NCSC’s guidance.
4. Clarification on including third party devices
All end user devices that your organisation owns and that are loaned to a third party must be included in the assessment scope. A new table is included for clarity on this subject
For devices not owned by your organisation, the table below explains what is in and out of scope: (use table from the requirements doc as the table should include crosses and ticks)
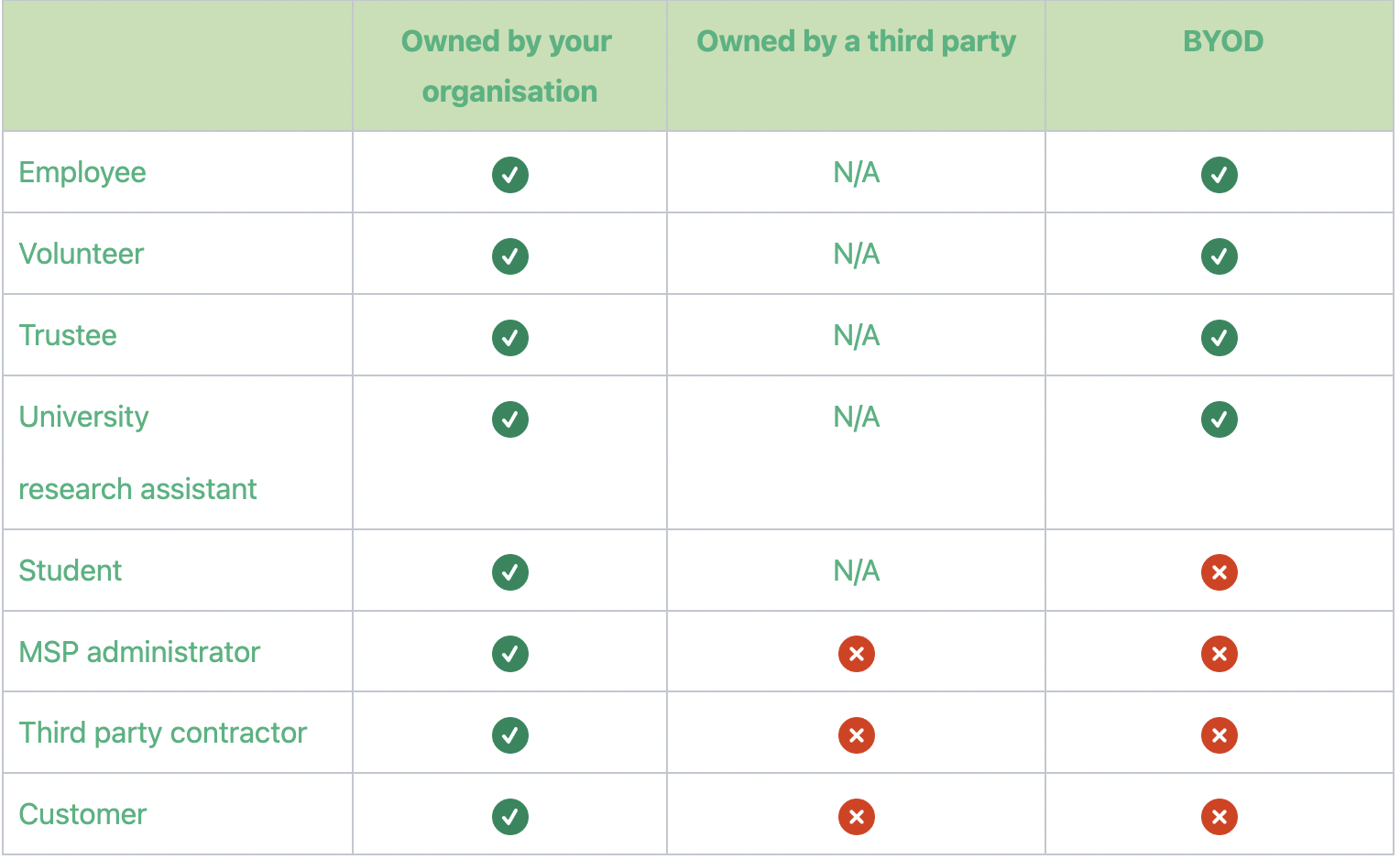
In scope = Green Tick
Out of scope = Red Cross
If you have questions surrounding these changes to the Cyber Essentials standard and how this may impact your accreditation/renewal please get in touch.
You can read our previous update here: Changes to Cyber Essentials – Evendine Has Arrived!
CyberLab Control | Cyber Security as a Service
Free 14-day Trial
Experience the beneifts of an all-in-one cyber security portal with a free 14 day trial.
No obligation, no credit card required.

CyberLab Named Finalist at Channel Champion Awards

