In the news: Cisco Routers, Twillio Breach, Draytek Routers and NHS Cyber Attack
Jack Smallpage, Information Security Officer at CyberLab, reviews the latest cyber security news and advises how to protect your data. He covers:
- Cisco hit again with Routers & ASA’s
- Twilio breached as Smishing campaigns catch people off-guard!
- Draytek Routers hit with a 10/10 vulnerability!
- NHS suffer a cyber attack outage
- CISA warns of UnRAR flaw exploited in the wild
- 9000+ VNC Servers Exposed online without passwords
Welcome back to another monthly instalment of our Security Month in Review. The security world is constantly moving and evolving, with vulnerabilities, breaches and new guidance being released daily. The volume and complexity of some of these can sometimes be overwhelming and challenging to keep track of, so let’s use this article to help summarise some of this month’s highlights so that together, we can be more cyber aware.
Cisco hit again with Routers & ASA’s
Cisco is a worldwide leader in networking solutions with their switches, routers and other solutions being common knowledge across IT sectors globally. Because of this, it is no wonder that their devices have become among the favourite targets of attackers. At the start of this month, Cisco released an advisory regarding two vulnerabilities found in their RV series routers that enabled an unauthenticated, remote attacker to execute arbitrary code and trigger denial of service conditions on the vulnerable devices.
The vulnerabilities lie within the web-based management interface of the routers. The attacker has to exploit both vulnerabilities in tandem due to their dependencies on one another.
It wasn’t just Cisco’s routers hit this month, either. One week later, they revealed a further advisory regarding a high severity vulnerability affecting its Adaptive Security Appliance (ASA) and Firepower Threat Defence (FTD) software. This time the vulnerability is in the handling of the RSA keys on devices running Cisco ASA and FTD software. If exploited, it would let an unauthenticated attacker retrieve an RSA private key remotely, allowing them to decrypt the device traffic or impersonate the device.
What Should I Do?
- RV Series Routers
There are no workarounds for this vulnerability, so the software updates released by Cisco should be applied as soon as possible. To check if you are affected and for more details, please find the advisory here: Cisco Small Business RV Series Routers Vulnerabilities
- Cisco ASA’s and FTD’s
If you believe you could be affected by this, make sure to visit the Cisco advisory to see the list of the affected products and apply the released software updates where applicable. The advisory also contains indicators of compromise to help admins check their networks for further peace of mind. The advisory can be found here: Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software RSA Private Key Leak Vulnerability
Twilio breached as Smishing campaigns catch people off-guard!
Twilio, the owner of the well-known and used two-factor authentication (2FA) provider Authy, were involved in a security breach this month which affected approximately 125 of their customers.
The unauthorised access was granted through a sophisticated social engineering smish (phishing via SMS) attack designed to steal and then use employee credentials. Whilst Twilio confirmed there is no evidence to suggest that customer passwords, authentication tokens, or API keys were accessed, other customer information were accessed and Twilio are still investigating to identify the full extent of the incident. They have revoked access to the compromised employee accounts to help mitigate the attack.
The smish attempt itself was sent to a variety of Twilio employees (both current and former) purporting to be from their IT department. The message suggested that the employees’ passwords had expired or their schedule had changed, and they needed to log into a URL to solve. The URL itself was cleverly crafted to look like a legitimate Twilio URL (see images below), which further took the victim to a realistically impersonated Twilio sign-in page.
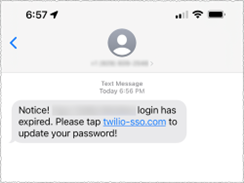
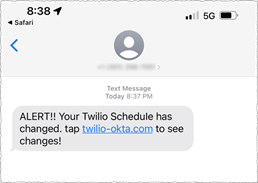
What Should I Do?
For those customers that have been affected, Twilio have been reaching out with the details. This attack further highlights the importance of strong phishing training and reporting culture within your business. Backed with the NCSC’s statistic of phishing being the most common attack vector at 83% of attacks, it’s quick wins like this that can have a massive impact on your business’ security. Make sure you’re testing your people’s awareness with training and simulations. Involve advanced techniques like spear-phishing and smishing to give your people the awareness of what these techniques look like. The regularity to ensure they are vigilant, but more importantly to develop a safe ‘no blame’ culture that empowers your people to report these things without reprimand. The quicker they report it, the quicker you can mitigate the damage!
More information on this incident can be found here: Incident Report: Employee and Customer Account Compromise – August 4, 2022 (twilio.com)
Draytek Routers hit with a 10/10 vulnerability!
It hasn’t just been Cisco routers that were hit this month either. Draytek released an advisory earlier this month regarding a critical unauthenticated remote code execution (RCE) vulnerability impacting 29 models of their DrayTek Vigor series business routers.
Tracked as CVE-2022-32548, the vulnerability carries a CVSS v3 score of 10.0 – the maximum on the scale and appropriately marked as ‘Critical’. The attacker does not need credentials or user interaction for the exploit and is viable via the internet but also via LAN in the device’s default configuration. Once exploited, attackers would be able to perform a complete device takeover, use the routers as DDoS bots, gain access to internal resources, and more!
What Should I Do?
If you think you could be impacted, make sure to check the DrayTek advisory here for a list of affected models: DrayTek Router unauthenticated remote code execution vulnerability (CVE-2022-32548) | DrayTek.
If you are affected, make sure to find and install the fixed version found here: Latest Firmwares | DrayTek with further guidance on this being found here: Upgrading Router Firmware using the Web Interface (draytek.co.uk).
It is also important if you are affected at this stage to investigate further for any potential indicators of compromise, such as any suspicious behaviour/activity from the routers using the security and monitoring tools at your disposal.
“Having used CyberLab before in a previous Head of IT role, I had no hesitation in engaging them again to assist us with our security needs. Simply, I wouldn’t use them if they didn’t consistently deliver value.”
– Head of IT, NHS
NHS suffer a cyber attack outage
The NHS‘s 111 service was hit earlier this month by a significant outage caused by a cyberattack on their Managed Digital Service Provider (MSP) ‘Advanced.’ 85% of NHS 111 services use the Adastra patient management solution for referring patients for care, ambulance dispatch, out-of-hours bookings and emergency prescriptions, and is just one of the services hit by the attack.
Now confirmed as a ransomware attack that caused the damage, Advanced has been working with Microsoft DART, NCSC and other forensic and security experts to recover and restore connectivity to their environments and ensure a safe and secure reconnection.
What Should I Do?
In an update, Advanced said that the following products were impacted:
-
- Adastra (Clinical Patient Management)
-
- Caresys (Care Home Management)
-
- Odyssey (Clinical Decision Support)
-
- Carenotes (Electronic Patient Record)
-
- Crosscare (Private Clinical Management)
-
- Staffplan (Care Management)
-
- eFinancials (Public Sector Financial Management)
Whilst it still isn’t known who was behind the attack or the method of compromise involved, this incident is another reminder amongst the hundreds past of the danger ransomware poses to your business and customers. Make sure to look into your supply chains and any reliance you have on MSP’s etc, and ensure they meet your security expectations. It’s also important to look at your own protections and ensure you have mitigations to prevent an occurrence but also a fast response plan for the situation where you protections are breached – more guidance on this can be found on the NCSC’s Ransomware guide here: A guide to ransomware – NCSC.GOV.UK
For Adastra’s Security Incident updates, look here: Cyber Incident Updates for Adastra | Advanced (oneadvanced.com)
CISA warns of UnRAR flaw exploited in the wild
CISA (U.S Cybersecurity and Infrastructure Security Agency) added a recently disclosed vulnerability in the UnRAR utility to its known exploited vulnerabilities catalogue this month due to evidence of active exploitation.
Tracked as CVE-2022-30333 and disclosed by Swiss company ‘SonarSource’, the vulnerability in RARLAB’s UnRAR utility for Linux and Unix systems uses path traversal to allow an attacker to plant a malicious file on a targeted system by extracting it to an arbitrary location during the unpack operation.
What Should I Do?
With evidence of active exploitation severe enough for CISA to enforce, it is important to check your systems for any instance of UnRAR versioned 6.11 or below and apply the advised patch as soon as possible. It is, however, useful to note that WinRAR and Android RAR are unaffected by this vulnerability.
CISA’s vulnerability catalogue can be found here: Known Exploited Vulnerabilities Catalog | CISA
The Vulnerability details can be found here: NVD – CVE-2022-30333 (nist.gov)
The UnRAR updates can be found here: WinRAR archiver, a powerful tool to process RAR and ZIP files (rarlab.com)
9000+ VNC Servers Exposed online without passwords
Researchers at Cyble have discovered at least 9000 exposed VNC endpoints in an article released this month. The endpoints identified can be accessed and used without authentication, giving attackers easy access to internal networks.
VNC is a graphical desktop-sharing system meant to help users connect to systems that require monitoring and adjustments, offering users remove control of another computer using the Remote Frame Buffer (RFB) protocol over a network connection.
It is easy to think your instances are secure without actually checking to confirm (as is likely the case with some of the 9000 detected here). Alarmingly, this research showed exposed instances of industrial control systems which should never have been exposed to the internet in the first place. It’s important to also note that this research focussed only on instances which had NO passwords. Still, instances with weak passwords are similarly trivial to crack and access and would increase the 9000 number even more!
What Should I Do?
Check to see if you utilise VNC within your network and make sure you properly assess the security risks involved with each instance of their use. Where VNC usage is necessary, make sure you:
-
- Prevent exposing servers over the internet, placing them behind a VPN where remote access is absolutely necessary.
-
- Ensure authentication is enabled with proper password strength guidance applied
-
- Enable MFA (Multi-factor authentication) where possible
-
- Placed behind a VPN
More detail on the research can be found on Cyble’s article here: Cyble — Exposed VNC a major threat to Critical Infrastructure Sectors
Conclusion
It’s been another busy month for security as the holiday season has been in full flow. With the NHS being hit with a cyberattack, and communications giant Twilio being compromised by a smish campaign, this month has highlighted that anyone can be hit with a cyberattack and we must all be prepared. With routers being exploited, VNC servers exposed and CISA’s vulnerability register growing, we must use this information to respond by fixing issues highlighted and identify areas to improve before the wrong people find them!
As always, it is important to reiterate that this article has not included ALL security news or vulnerabilities disclosed this month. Others such as Microsoft’s Dogwalk Patch Tuesday 0-day fix, Exim’s RCE vulnerability, VMware’s critical authentication bypass, and Apple’s latest 0-day security update are just honourable mentions as examples of other updates you should be aware of and research.
If you have been caught off-guard by some of this month’s developments, look at your security processes and see what changes you can make to ensure you don’t get caught out in the future. Just 20 minutes research each day can help you keep on top of the significant security trends and alerts, which help protect your business and keep you cyber aware! If you have any more questions or worries, please do not hesitate to get in touch and see what CyberLab can do to help you and your security posture.
Book your consultation today.
Detect. Protect. Support.
Posture Assessment
Understand your security risks and how to fix them.
Take the first step to improving your cyber security posture, looking at ten key areas you and your organisation should focus on, backed by NCSC guidance.
Claim your free 30-minute guided posture assessment with a CyberLab expert.



Leave a Reply
You must be logged in to post a comment.