Active Monitoring Keeps You Secure
Gavin Wood, CEO at CyberLab, takes a trip down memory lane, summarising his years of experience in the industry and the new level of protection all organisations need.
He covers:
- The Dark Ages of IT: His first experience with an antivirus
- Email viruses: ILOVEYOU or Love Bug
- The emergence of Malware
- Introduction of NextGen Antimalware
- Active Monitoring: The new norm of security protection
“There are only two types of companies: Those that have been hacked and those that will be hacked.”
– Robert S. Mueller, III, former Director of the FBI
I was recently asked about the changes that I have seen in the IT and IT Security industry since I started work, which really made me think.
The Dark Ages of IT: My first experience with an antivirus
Back in probably what seems like the dark ages technically speaking, business IT systems were almost exclusively the domain of the SysAdmin with green screen terminal access for the “users”. Large mainframe systems took up whole rooms. I was expecting a mission control type setup with terminals, flashing lights, reel to reel tapes spinning in cabinets with transparent fronts. The reality was a large, black, plastic box, about the size of a large dining table with just four tiny green flashing lights on it. Not as spectacular as I had imagined, although what this system could and did indeed do was very cutting edge at the time.
Through the years that I worked for that same company, cutting my teeth as a SysAdmin, that same black box became smaller and smaller. It eventually could be housed in a standard 19″ rack that you will see in data centres worldwide.
When email started to emerge as a business communication method, we had to go and ask the “marketing guy” to send an email on our behalf. He had the only modem in the whole company. This wasn’t a small organisation at all!
To protect this precious communications device, we had installed one of the first antivirus software applications. We received updates through the post at regular(ish) intervals. We had to load them onto that same device time manually, time and time again. Back then, this was the best protection we could offer our business against the threat landscape.
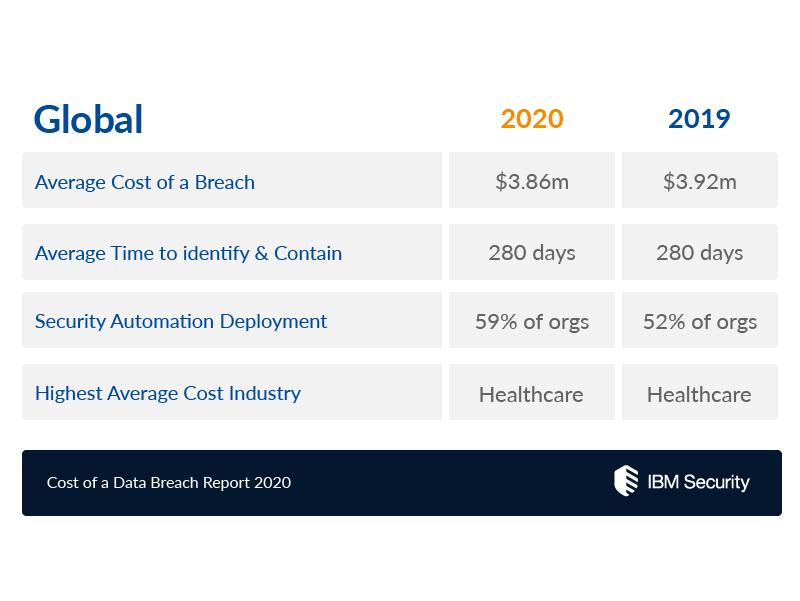
Email viruses: ILOVEYOU or Love Bug
Jumping forward a few years, PCs had replaced most of the usual terminals on people’s desks, and antivirus had matured. We had the basic capability to download an update manually, but it still had to be distributed by hand as only a handful of machines had direct internet access.
Even with no direct internet access on most machines, everyone had an email address. People were able to send and receive emails, but the threat from a virus was present. If anyone hasn’t heard of the ILOVEYOU or Love Bug virus, a quick read of the wiki article on it is worth it. It’s interesting because it uses an early form of what is known now as social engineering.

Malware emerges
Jumping forward yet again, threats from Malware became constant. Any machine connected to the internet was at risk from a virus. This is when the term Malware emerged.
Antimalware packages got more sophisticated as the threat got greater and more easily spread. These products took on additional characteristics to protect the devices:
- Scanning downloads
- Checking for malicious scripts on web pages
- Preventing new dial-up connections
- Blocking and scanning USB devices
Incremental improvements were made to Antivirus/Antimalware applications over time. Threat researching become quicker, using advanced automation techniques. Due to the exponential rise in Malware, antimalware providers produced signature files at pace and client/server setups allowed for the rapid deployment across the network at very regular intervals.
NextGen Antimalware is introduced
The next big leap is the jump to what we now know as NextGen Antimalware. These solutions typically use an AI trained model to identify and block threats without the need for an already written signature. This is great news! No longer does an antimalware provider need to write signatures and distribute them as threats emerge (although this still happens and is another essential layer in defence). The actual application itself blocks the threat automatically using behavioural traits.
Another change you will have noticed is the name change from Antimalware to Endpoint protection. These products protect and secure multiple endpoint types (desktop, laptop, server, mobile phone, tablet), offering much more capability than antimalware services. These NextGen technologies also include AntiRansomware components, critical of any Endpoint protection software.
True business-grade NextGen Endpoint protection is great if properly configured. However, the latest serious threats come from much more sophisticated attacks than spray and pray types that get blocked by a good NextGen solution.
Sophisticated attacks will involve reconnaissance work. Then targeted attempts to infiltrate a system or network will take place. The aim is to trigger a payload such as Ransomware to steal information or IP from your organisation.
Active Monitoring: The new norm of security protection
Going back to the quote at the beginning of this article… The only way to know exactly what is going on in your network or on your devices is with active monitoring.
That’s where the current NextGen Endpoints are at now. Technologies such as EDR (Endpoint Detection and Response) or MDR (Managed Detection & Response) are services specifically designed to look for abnormal activity on a network, no matter how seemingly insignificant, and allow you to deal with these potential threats.
EDR is a fantastic tool if your team can take advantage of these technologies. However, considering the shortage of skilled cybersecurity professionals, that can be a massive challenge for organisations. To really see the value of an EDR solution, you’d need to consider who will manage it in-house.
Four out of five organisations are struggling with threat detection and response due to lack of security expertise.
Source: 7 uncomfortable truths of Endpoint Security, Sophos Report, 2019
If you don’t have the resource, MDR is effectively someone running these EDR services for you, 24 x 7 x 356. Actively monitoring your endpoints, using all the tools, services, and experience to ensure if something suspicious is happening, it is caught, stopped, remediated, and you’re protected against it.
I believe that EDR and MTR solutions should be the minimum level of protection for endpoints in today’s world. A quick read of the technology press will show the millions paid regularly to hacking groups. These could have been stopped if caught earlier in the attack chain using EDR and MTR technologies.
Detect. Protect. Support.
Sophos MDR
Where others stop at notification, Sophos MDR takes action.
Few organisations have the right tools, people, and processes in-house to manage their security program around-the-clock while proactively defending against new and emerging threats.
Sophos MDR provides you with an elite team of threat hunters and response experts who take targeted actions on your behalf to neutralise even the most sophisticated threats.

5 Cyber Security Predictions for 2026

Leave a Reply
You must be logged in to post a comment.